It was early morning in India when Apple held a briefing to discuss its updated Platform Security Guide (a guideline of how Apple secures its products and services across the platform at all levels – Hardware, Software and Services). The Apple Platform Security Guide is now a good 200 odd pages and covers the latest security advancements across macOS Big Sur, iOS 14, iPadOS 14, watchOS 7, and tvOS 14. For me, it was nothing less than reading a holy book, reading each word religiously and understanding in absolute detail how things like – Touch ID, Face ID, Secure Boot, File Vault and etc work.
While you can download and read all of it in detail from the Apple website by downloading the Platform Security Guide or visiting the Apple Support website. I want to quickly point out the major changes and then share an example of something as simple as Face ID that we use day in, day out.
So the significant changes in this year’s Platform Security Guide have to do with Apple Silicon (M1). The new sections outline the security of the boot process, boot modes, startup disk, Rosetta 2 translation process for running Intel-based Mac apps, FileVault, Activation Lock, and more.
Do check out all the new topics added to the Apple Platform Security guide this year:
- Memory safe iBoot implementation
- Boot process for a Mac with Apple silicon
- Boot modes for a Mac with Apple silicon
- Startup Disk security policy control for a Mac with Apple silicon
- LocalPolicy signing-key creation and management
- Contents of a LocalPolicy file for a Mac with Apple silicon
- Signed system volume security in macOS
- Apple Security Research Device
- Password Monitoring
- IPv6 security
- Car keys security in iOS
And these are the security topics that have been updated:
- Secure Enclave
- Hardware microphone disconnect
- recoveryOS and diagnostics environments for an Intel-based Mac
- Direct memory access protections for Mac computers
- Kernel extensions in macOS
- System Integrity Protection
- System security for watchOS
- Managing FileVault in macOS
- App access to saved passwords
- Password security recommendations
- Apple Cash security in iOS, iPadOS, and watchOS
- Secure Business Chat using the Messages app
- Wi-Fi privacy
- Activation Lock security
- Apple Configurator 2 security
Along with updating the Platform Security Guide, Apple also has a new Security Certifications and Compliance Center.
Now let’s talk, Face ID.
What may seem like a quick and simple scan of your face (Face ID) to unlock your device is a rather complex set of actions that take place under the hood.
How Face ID security works?
With a simple glance, Face ID securely unlocks supported Apple devices. It provides intuitive and secure authentication enabled by the TrueDepth camera system, which uses advanced technologies to accurately map the geometry of a user’s face. Face ID uses neural networks for determining attention, matching, and antispoofing, so a user can unlock their phone with a glance. Face ID automatically adapts to changes in appearance, and carefully safeguards the privacy and security of a user’s biometric data.
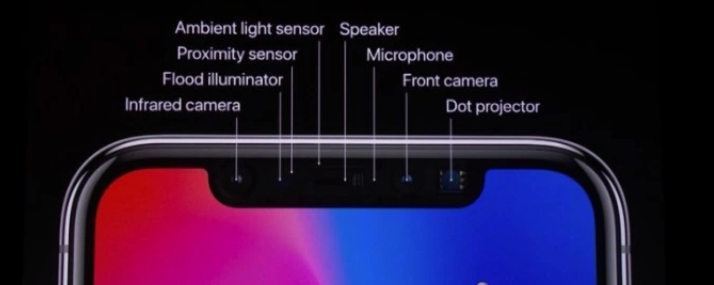
Face ID is designed to confirm user attention, provide robust authentication with a low false match rate, and mitigate both digital and physical spoofing. The TrueDepth camera automatically looks for the user’s face when the user wakes an Apple device that features Face ID (by raising it or tapping the screen), as well as when those devices attempt to authenticate the user in order to display an incoming notification or when a supported app requests Face ID authentication. When a face is detected, Face ID confirms attention and intent to unlock by detecting that the user’s eyes are open and their attention is directed at their device; for accessibility, the Face ID attention check
is disabled when VoiceOver is activated and, if required, can be disabled separately.

After the TrueDepth camera confirms the presence of an attentive face, it projects and reads over 30,000 infrared dots to form a depth map of the face along with a 2D infrared image. This data is used to create a sequence of 2D images and depth maps, which are digitally signed and sent to the Secure Enclave. To counter both digital and physical spoofs, the TrueDepth camera randomizes the sequence of 2D images and depth map captures and projects a device-specific random pattern. A portion of the Secure Neural Engine—protected within the Secure Enclave—transforms this data into a mathematical representation and compares that representation to the enrolled facial data. This enrolled facial data is itself a mathematical representation of the user’s face captured across a variety of poses.
Facial matching security
Facial matching is performed within the Secure Enclave using neural networks trained specifically for that purpose. Apple developed the facial matching neural networks using over a billion images, including infrared (IR) and depth images collected in studies conducted with the participants’ informed consent. Apple then worked with participants from around the world to include a representative group of people accounting for gender, age, ethnicity, and other factors. The studies were augmented as needed to provide a high degree of accuracy for a diverse range of users. Face ID is designed to work with hats, scarves, eyeglasses, contact lenses, and many types of sunglasses. Furthermore,
it’s designed to work indoors, outdoors, and even in total darkness. An additional neural network—that’s trained to spot and resist spoofing—defends against attempts to unlock the device with photos or masks. Face ID data, including mathematical representations of a user’s face, is encrypted and available only to the Secure Enclave. This data never leaves the device. It’s not sent to Apple, nor is it included in device backups. The following Face ID data is saved, encrypted only for use by the Secure Enclave, during normal
operation:
• The mathematical representations of a user’s face calculated during enrollment
• The mathematical representations of a user’s face calculated during some unlock attempts if Face ID deems them useful to augment future matching
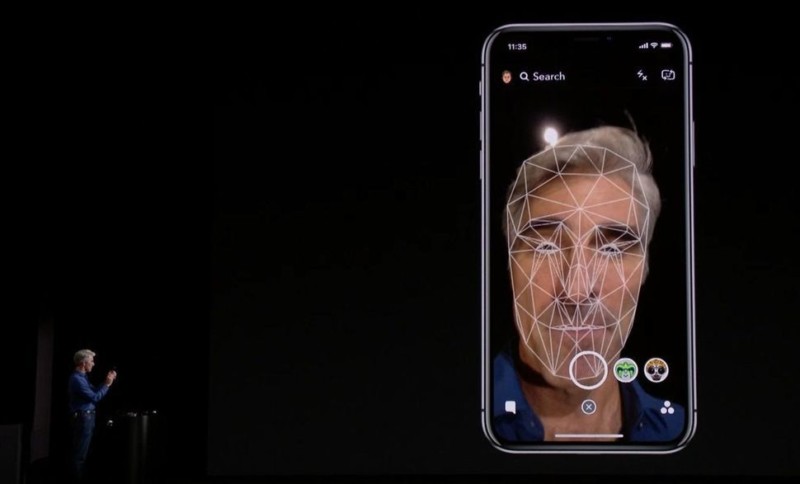
Face images captured during normal operation aren’t saved but are instead immediately discarded after the mathematical representation is calculated for either enrollment or comparison to the enrolled Face ID data.
Improving Face ID matches
To improve match performance and keep pace with the natural changes of a face and look, Face ID augments its stored mathematical representation over time. Upon a successful match, Face ID may use the newly calculated mathematical representation—if its quality is sufficient—for a finite number of additional matches before that data is discarded. Conversely, if Face ID fails to recognize a face but the match quality is higher than a certain threshold and a user immediately follows the failure by entering their passcode, Face ID takes another capture and augments its enrolled Face ID data with the newly calculated mathematical representation. This new Face ID data is discarded if the user stops matching against it or after a finite number of matches. These augmentation processes allow Face ID to keep up with dramatic changes in a user’s facial hair or makeup use while minimizing false acceptance.
So now you know how Face ID works and how safe it is. Over the course of the next few days will be sharing more such topics from the Apple Platform Guide. Do let us know if you want to know about something specific in the comments section below or tweet to us @theunbiasedblog











