In a recent Microsoft sweep of PC, test purchasing revealed that more 83%(four in five) brand new PCs in targeted countries in Asia are loaded with pirated software. The PC samples selected were purchased from retailers that offered PCs at much lower cost and free software bundles to lure customers. In many cases, these retailers also sold pirated software at their store. Microsoft’s Asia PC Test Purchase Sweep is aimed to educate consumers and owners of small and medium enterprises (SMEs) in the region.
The Risks of Using Pirated Software
The sweep found that one of the most common practices for vendors installing pirated software on new PCs is to turn off the security features, such as anti-virus software and Windows Defender as doing this allows them to run the hack-tools needed to activate the pirated software. However, this leaves PCs vulnerable to malware and other cyber threats, and the buyers of these PCs may not even realize that their PC is not being protected.
The sweep also uncovered that 84% of the new PCs loaded with pirated software were infected with some type of malware, with the most common malware being Trojans and viruses.
- Trojans are a type of malware that is employed by cybercriminals to gain remote access and control of devices, allowing them to spy on the users and steal private data. While Trojans typically depend on some form of social engineering to trick users into loading and executing them, bundling them with pirated software makes it easier for cybercriminals to compromise and control PCs.
- Viruses are another type of malware which can cause infected computers to do a variety of things which are not beneficial to the PC owner, such as terminating devices’ security features, sending spam messages, and contacting remote hosts to download additional malware.
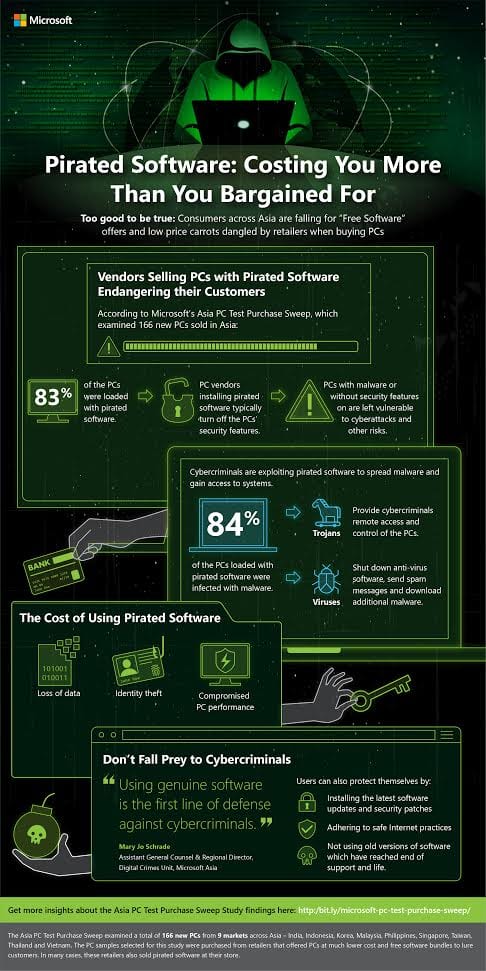 These findings are particularly concerning as customers new PCs come with free software. Many of these infected PCs’ users are highly susceptible to data loss, including personal documents and sensitive information such as passwords and banking details, as well as identity theft where they lose control of their social media and email accounts. Users might also experience compromised PC performance as malware, running in the background, can slow down devices. All these factors can lead to consumers and businesses chalking up significant monetary, time and productivity losses as they work to resolve the issues.
These findings are particularly concerning as customers new PCs come with free software. Many of these infected PCs’ users are highly susceptible to data loss, including personal documents and sensitive information such as passwords and banking details, as well as identity theft where they lose control of their social media and email accounts. Users might also experience compromised PC performance as malware, running in the background, can slow down devices. All these factors can lead to consumers and businesses chalking up significant monetary, time and productivity losses as they work to resolve the issues.
Key Cyber-Hygiene Practices for Individuals and SMEs
The most fundamental step that users can take to safeguard themselves digitally is to always insist on buying PCs from established retailers and not ones that also sell pirated software, and ensuring they are getting genuine software. Consumers should refer to software vendors’ websites to learn how they can distinguish between genuine and pirated software.
Besides using genuine software, people can also consider and adhere to the following recommendations to better protect themselves:
- Keep software current with the latest security patches, which are always free.
- Follow safe Internet practices and do not visit potentially dangerous websites, such as those that offer adult content, illegal downloads, and pirated software, as well as file sharing portals.
- Avoid using very old software which has reached its end of life and is no longer supported by the software vendor for updates and security patches.
Follow us on twitter for more news and update.











