Last year WannaCry created havoc across the globe and due to its lateral movement, it had penetrated into the networks and skipped across the countries and continents. Also, the security community has been highly proactive in taking down the infrastructure associated with WannaCry, however, due to its ability to move across networks, eScan observes that it still exists in its dormant form.
eScan’s telemetry servers have been picking up reminiscent artefacts of WannaCry Ransomware on regular basis. Over the period of last few months, we have observed a steady decrease of incidents involving WannaCry and hopefully, by the year-end, WannaCry should meet the same fate as that of Conflicker Worm / DNS Changer Botnet, said the company. 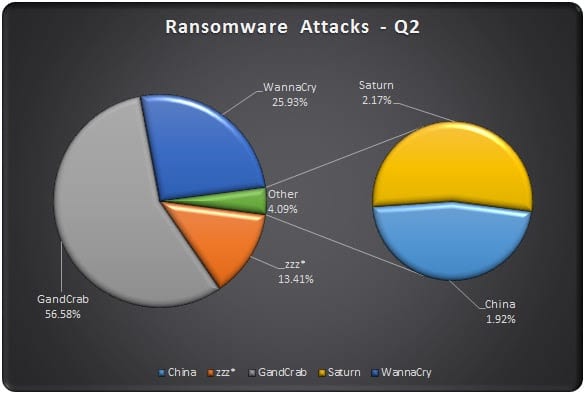

We have been observing various variants and newer Ransomware being added into the family, however very few have seen active development, viz. GandCrab and ZZZ. In last few weeks, GandCrab has taken a center-stage and is evolving at a much faster rate, which suggests that the Ransomware Developer / Criminal nexus is growing stronger and many of the criminals are now switching their loyalties to GandCrab due to the sheer fact that the developers are taking keen interest and adding numerous weapons to its arsenal.
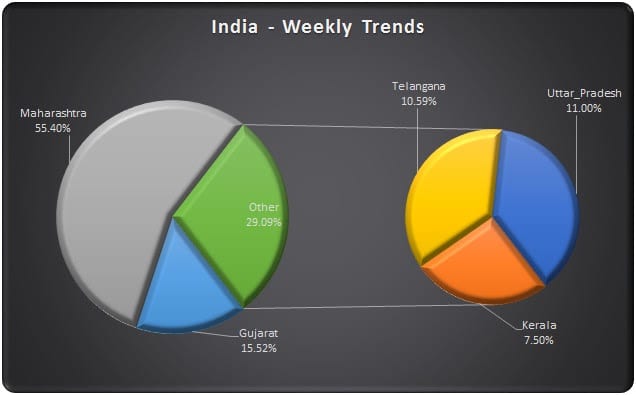
India has seen its share of Ransomware attacks and Maharashtra leading the way for the week, however, in states like Gujarat, Telengana, Uttar Pradesh and Kerala we have observed a rise in activity of the GandCrab Ransomware Attacks while xtbl, korean, Dharma and CrySiS variants of Ransomware family are still making rounds.
Prevention Measures:
- To stay safe from such ransomware attacks, all the organizations and users need to ensure that, the patches released by Microsoft have been updated or patched immediately.
- Administrators should block all executable files from being transmitted via eMails.
- Administrators should isolate the affected system in the Network.
- The administrator can restore the encrypted files from the backup or from system restore point (if enabled) for affected systems.
- Install and Configure eScan with all security modules active: eScan Real-Time Monitoring, eScan Proactive protection, eScan Firewall IDS/IPS Intrusion prevention
- Users shouldn’t enable macros in documents.
- Organizations should deploy and maintain a backup solution.
- Most important, Organizations should implement MailScan at the Gateway Level for mail servers, to contain the spread of suspicious attachments.
Follow us on Twitter for more news and updates.